Using Security Groups for Pods in Amazon EKS
Description
Containerized applications frequently require access to other services running within the cluster as well as external AWS services, such as Amazon Relational Database Service (RDS).
On AWS, controlling network-level access between services is often accomplished via security groups.
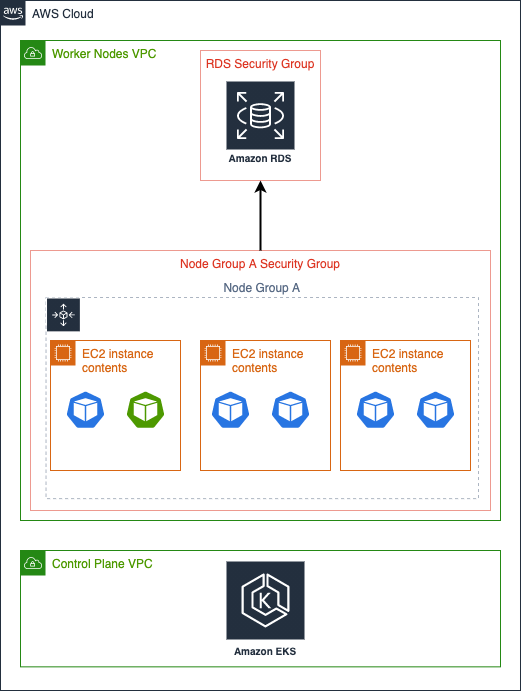
Early versions of EKS only allowed you to assign security groups at the node level. Because all nodes inside a node group share the security group, by attaching the security group to access the RDS instance to the node group in the image below, all the pods running on these nodes would have access to the database even if only the green pod should have access:
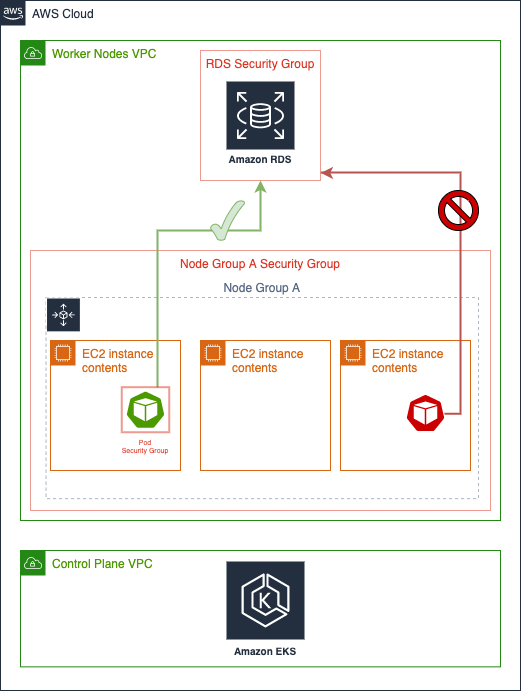
Security groups for pods integrate Amazon EC2 security groups with Kubernetes pods. You can use Amazon EC2 security groups to define rules that allow inbound and outbound network traffic to and from pods that you deploy to nodes running on many Amazon EC2 instance types. In this lab, you will learn how to integrate security groups with an EKS cluster to access an RDS database and demonstrate the effect of Pod security groups as shown in the following environment diagram:
Learning Objectives
Upon completion of this lab, you will be able to:
- Configure Amazon EKS node groups to use trunk network interfaces to enable pod security groups
- Use SecurityGroupPolicy custom resources to select pods that are associated with security groups
- Identify network interfaces protected by security groups
- Demonstrate the effects of security groups per pod
Intended Audience
- Kubernetes practitioners, especially those working with Amazon EKS
- DevOps Engineers
- SREs
Prerequisites
Familiarity with the following will be beneficial but is not required:
- Basic Linux command line administration
- Basic Kubernetes and Container-based concepts
- Familiarity with AWS resources including VPCs and security groups
The following content can be used to fulfill the prerequisite:
- Linux Command Line Byte Session learning path
- Introduction to Kubernetes learning path
- Working with AWS Networking and Amazon VPC course
Updates
October 11th, 2024 - Updated Kubernetes version
May 20th, 2024 - Resolved issues regarding deployments and permissions
December 5th, 2023 - Updated Kubernetes version
February 28th, 2023 - Updated to k8s 1.24
Covered topics
Lab steps
- Logging In to the Amazon Web Services Console
- Connecting to the Virtual Machine using EC2 Instance Connect
- Installing Kubernetes Management Tools and Utilities
- Introducing Security Groups for Pods
- Creating and Configuring the Security Groups
- Creating the RDS Database
- Configuring the CNI
- Creating a SecurityGroupPolicy Custom Resource
- Testing the SecurityGroupPolicy
- Cleaning up the Pod Security Group Lab Resources